What with choosing passwords that are hard to guess, maintaining different passwords for different services, and changing passwords periodically, you probably think you can’t keep track of everything without writing all your passwords down somewhere. Although writing passwords on slips of paper is a time-honored tradition, it’s one of those traditions that’s best eliminated, especially because better alternatives are available.
The Mac OS has a built-in feature called the keychain that helps you manage your passwords in an easy, secure way. The keychain is pretty much what it sounds like: a place where you put all your keys (in this case, passwords) for easy access when you need them. When you go to a door that needs a key (a Web site that has a password, for example), you or the application can get the needed key from the keychain and unlock the door (or gain access to the site).
To get started using the keychain with Mac OS X, you really don’t need to do anything. The first time you log into your Mac (or simply start your Mac if you’re the only user), a default keychain (your login keychain) is automatically created, and each successive time you log in, your login keychain is automatically unlocked (unless you turn off this feature; see below). Whenever you first enter a password to access an Internet service, an entry for that service can often be added to your login keychain. The master password for your login keychain starts out as the same one you use to log in, or the one you specified when you first started your Mac if you don’t log in.
Additional keychains can be useful for specific sets of passwords. For example, you might want to use the login keychain for routine daily operations, and have a separate keychain for online shopping. To create a new keychain, go to the Utilities folder within the Applications folder and launch the Keychain Access application. From the File menu, choose New Keychain (Figure 4.2).

Figure 4.2 Creating a new keychain to manage your passwords
You will be prompted for a name for the new keychain, and a location on disk to store the keychain file – it is recommended that you use the default location. Next you will be prompted for a master password for the new keychain. This password will be used to provide complete access to all the passwords stored by the keychain, so it’s even more important than normal that you choose and maintain this password carefully. The keychain even warns you if it detects what it considers to be a poorly chosen password (Figure 4.3). In Mac OS 10.4, you can use the Password Assistant (Figure 4.1) to help you choose good passwords for your keychains.
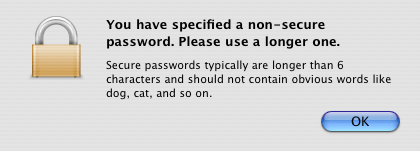
Figure 4.3 Choosing a good keychain password is critical, since that password can provide access to all the passwords on your keychain. The keychain will warn you if you seem to be choosing a password that is easy to guess.
The keychain is a good idea in principle, but it requires special features from most of the applications that want to use it, and some current applications don’t have the needed support. Those applications that do support the keychain include the Finder’s “Connect to Server” command and Network browser (which connect to AppleShare, Personal File Sharing and Windows Sharing servers), Mac OS X’s Mail application and Apple’s Disk Utility and iChat applications. Third-party keychain-aware applications include Eudora and Microsoft Entourage. The keychain also has limited built-in support for passwords associated with Web sites, but only certain Web sites work with the keychain. You can use the keychain to store passwords for sites that ask for a password through an HTTP dialog box before any part of the site comes up. Some Web browser, including Safari, can also use the keychain to store passwords for many sites that ask you to enter the password in a form, although not for all of them.
Another problem with the keychain is that it can put all your eggs in one basket. Just as you’re in big trouble if you put all your keys on a physical key chain and then lose the key chain, if you put all your passwords on the Mac keychain and then “lose” it, you’ll be in big trouble too. Losing the keychain could mean forgetting the master password that you use to unlock it or, worse, having that password compromised. In the latter case, someone else would have access to all your passwords if they have physical access to your machine. (Hackers should not be able to access the keychain over the Net, even if they have your master password, but you can never be 100 percent sure.)
An additional risk is that while your keychain is unlocked, anyone who has physical access to your machine potentially has access to all the services on your keychain. Whenever you start your machine, your keychain is unlocked automatically if it uses the same password that you use to log in. Even if your machine is set up for automatic login, you still have a login password, and the keychain will be unlocked at startup if it uses that password (which it’s set to do by default). This ease-of-use feature means that, unless you change things, anyone who has physical access to your machine can access the services for which you have passwords on your keychain.
After installing Mac OS X, run the Keychain Access utility, and change your keychain password to something other than your login password or set up the keychain to lock automatically after a specified period and when the system sleeps (Figure 4.4).
Apple has done a good job of mitigating some of the risks involved with the keychain. If someone walks over to your machine, for example, he may be able to access services through your passwords but he can’t see what those passwords are without knowing your master keychain password. To prevent unauthorized service access, any time you leave your machine, you can lock the keychain, and the master password must be re-entered before any keys are available. You can also set the keychain up to lock automatically after a specified period or any time your machine goes to sleep (Figure 4.4). Finally, the keychain can warn you any time an application tries to access any of the passwords it contains, protecting against rogue applications such as Trojan horses. (See Chapter 11 for details about Trojan horses.)

Figure 4.4 Setting important keychain security features.
Keychains and .Mac
Starting with OS X 10.4, it is possible to sync keychains through your .Mac account. This can be useful for backing up your keychains, or as a way to move keychains from one machine to another. Synchronization of keychains is done with the .Mac pane of System Preferences, in combination with Keychain Access (Figure 4.4). In the Sync tab of this pane you can specify manual or automatic backup at specified intervals. Even though you have presumably specified good master passwords for each of your keychains, storing such sensitive information on .Mac means your .Mac password should also be an especially good one. See Chapter 9 for details and risks associated with syncing your keychain through .Mac.
Other password-management techniques
Another good password-management application is Web Confidential. You can download the Web Confidential shareware application from http://www.web-confidential.com/. You use it much like the keychain to keep track of your various passwords. Web Confidential can track many passwords in various categories, even passwords for non-Internet items such as your ATM PINs. Like the keychain, Web Confidential has built-in integration with your Web browser, supporting both dialog-box-based and form-based site passwords (Figure 4.5).

Figure 4.5 The Web Confidential main window for managing passwords.
Web Confidential can invoke and receive information from certain applications automatically. It even integrates well with the keychain, so you can use both applications together. Caveats similar to those for the keychain apply, such as the risks associated with an “all your eggs in one basket” approach.
You can also manage your passwords without a password-management application, even if you have many passwords. Most applications that require passwords allow you to save those passwords within the applications themselves. In many cases, saving passwords within applications makes sense; in other cases, it doesn’t.
Saving passwords is especially useful in e-mail applications, for three reasons:
· You probably check e-mail often (perhaps even automatically), so it saves you from typing the password all the time (as well as avoids the risk of disclosure due to shoulder surfing).
· It saves you from having to remember e-mail passwords, especially if you have multiple accounts.
· If someone else gets hold of the e-mail application (and your saved password), the worst he can do is read your e-mail, assuming that you don’t use the same password for other services. He could also send e-mail as you, but it’s unfortunately easy to do this anyway (see Chapter 5).
Some e-mail applications, like OS X’s Mail, save your passwords unless you specifically tell them not to. Other e-mail applications, like Eudora (Figure 4.6), give you the choice of saving or not saving a mail account’s password. Both Mail and Eudora use the keychain to store their passwords.
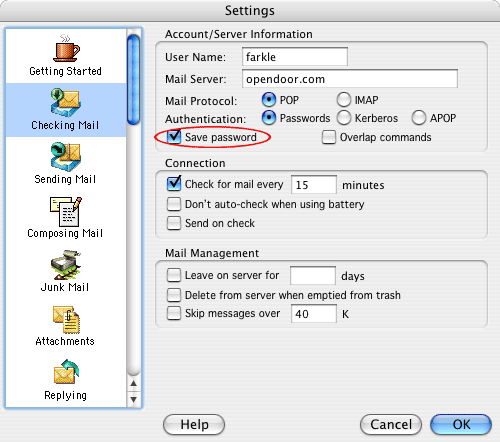
Figure 4.6 The save password option in Eudora
You can also use your Web browser to save your passwords to certain Web sites, and certain Web sites have their own ways of saving your password. Doing so is less advantageous than it is with e-mail, however:
· You probably don’t go to specific Web sites as often as you read your mail.
· Different Web sites have different password schemes, so saving your password may not work all the time.
· You may have greater exposure if someone gets access to your Web browser and, hence, to the Web sites for which you’ve saved passwords.
Other applications that save passwords may have similar risks, so evaluate each application based on its advantages and disadvantages.
One additional general warning: Don’t save passwords in applications on notebook computers that you travel with, at least not passwords for any important services. The risk of loss and password compromise is too high.
Another way to manage passwords is a level-of-protection system. As we’ve said in Chapter 2, you should always consider the risk involved with what you’re protecting in terms of how much work (and expense) you should use to protect it. You can take advantage of this principle by grouping your passwords in levels of protection. Here are some examples:
· Some Web sites ask for account names and passwords solely for their benefit, to track you as a user. In these cases, you wouldn’t care if someone else were to get your password.
· You can often get away with saving your e-mail passwords within your e-mail application, partly because the risk involved generally is low. If someone got your e-mail password and managed to read your e-mail, you would suffer a loss of privacy but, in general, no significant personal or financial loss.
· If someone got the password to a Web site that you and your family use for online banking, that situation could be very bad.
· You might have passwords that you don’t even want anyone in your family to know about—passwords for logging onto a Macintosh that you all share, for example, or passwords that you consider to be critically important, such as your keychain master password or one that enables your Macintosh to be controlled remotely over the Internet (see Chapters 9 and 10).
Because your password-protected services fall into different levels of protection, you can group your passwords and thereby make them easier to remember. You could use the following scheme for the four cases in the preceding list:
· For Web sites that ask for a password solely for their own benefit, use something that’s easy to remember and in fact violates most of the rules about good passwords—just your initials, for example. Use that same password for all such Web sites. Why waste brain cells remembering passwords that you don’t want to have in the first place?
· For e-mail passwords, whether or not you save them in the application, keep the passwords simple and consider using the same passwords for different accounts if you have them.
· For important family-related Web sites, follow all the password-choosing rules, but keep in mind that in certain rare situations, you may need to share these passwords with a good friend or family member.
· Your most critical passwords should be the hardest for anyone else to guess, and you should never share them with anyone under any conditions. Also, you should type these passwords only when you’re sure no one else is around. If an exceptional condition causes one of these passwords to be shared or potentially compromised, you should change it as soon as possible.
With a level-of-protection scheme, you can ensure that the highest levels of protection are being applied to the most important services and still maintain your passwords in a manageable fashion.
Finally, writing passwords down is generally a bad idea. But that’s principally because of what we do after we write our passwords down: We stick the password on the computer monitor. This may work for the Web sites that have passwords solely for their own benefit, but you shouldn’t do this for any service that you want to keep secure.
On the other hand, if you write a password down and then lock it in a safe or place it in a safe-deposit box, it’s more secure than it would be if it were saved in an application. The written password also serves as a backup in case you forget an important password, and it will be available to your loved ones when you’re no longer around. Especially if you seldom need the password, writing that password down and storing it in a secure place may make a lot of sense.
Dealing with forgotten passwords
No matter which password-management system you use, and no matter how much work you do, you’re going to forget or lose a password. You may make up a very difficult password and save that password in an application. Then you may upgrade that application and lose your password. (This situation shouldn’t happen, but it could.) Or perhaps you don’t use a service for a year and don’t remember the password when you go back.
You have several options for dealing with forgotten passwords. How you deal with a forgotten password often depends on the level of importance you place on the service involved:
For passwords that you use solely for the benefit of a Web site, simply create a new account and password for yourself. You might want to do this periodically even if you don’t forget your password, just to prevent the Web site from obtaining detailed tracking data on you (which is a privacy issue).
For medium-security services such as e-mail, consider contacting your e-mail provider and asking it to change your password to a new one. Your provider probably will require some proof of your identity (it should, anyway), but because the service is not a critical one, providing proof should not be a lot of work. Often, the provider can identify you through caller ID.
Some services (including Mac OS X’s login) ask you to provide a password hint when you first sign up, and use that hint to help you remember your password. If you use the hint, be sure that it’s something only you can figure out.
For high-security services, you’re probably going to have to do a lot of work to recover the password. In many cases, starting from scratch with another account may be better. Doing so may not be practical in many cases, however, such as with a bank account with real money in it. In such cases, you might want to plan ahead, write the password down, and store it in your safe-deposit box, in anticipation of such a problem. Going to your safe-deposit box could be a lot less work than going down to the physical business involved or going to a notary public in an attempt to persuade a particular business that you’re really you.